App e MyDaze web portal
No matter how complex your installation. We have the right solution for your remote management.
5-star customer service
For us, your satisfaction is everything. And we prove this not only with the quality of our product, but also with our customer care team always ready to assist you in a timely manner.
Electric in progress
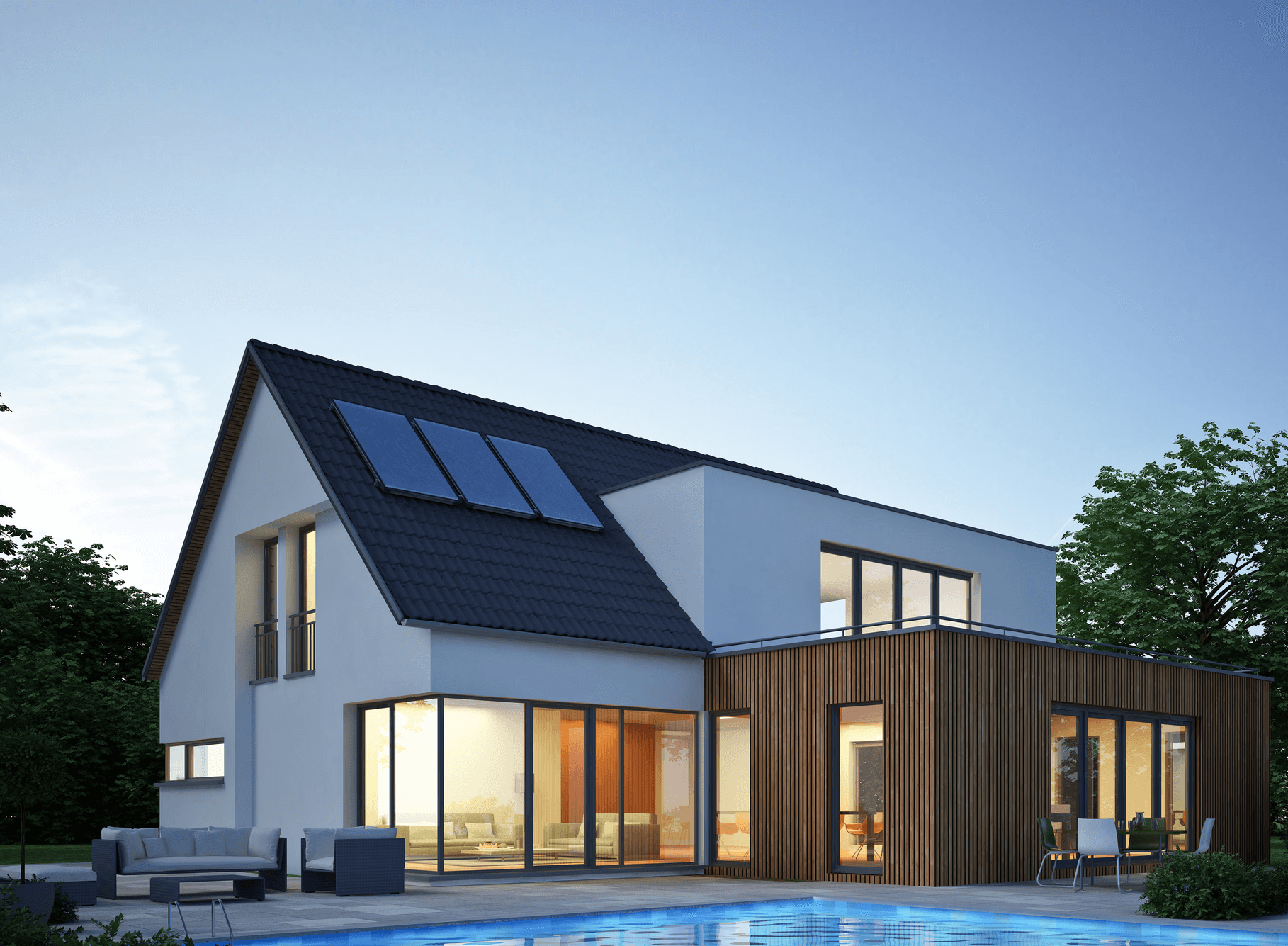
Solar panels and hail: everything you need to know to protect the system
Hail and photovoltaic panels: how to protect them, recognize damages, choose the right insurance, and evaluate technical certifications.
Jul 10, 2025
Read
How to be electric
Smart parking system: how it works and why it revolutionizes mobility
Discover how a smart parking system works and why it improves urban and business mobility. Intelligent solutions for stress-free parking.
Jul 9, 2025
Read
How to be electric
How to plan an electric car trip in 2025
Organizing a trip in an electric car is not complicated; you just need to know where to start. From managing autonomy to choosing stops, this guide helps you understand how to approach each stage with peace of mind.
Jul 8, 2025
Read